One of the chores I find myself regularly doing when working on a new project is creating static HTML front-end website’s for the Serverless backend’s I work on.

Dependency injection is a powerful technique that can be applied in many situations across all layers of an application. But this does not mean that dependency injection should be used every time a class depends on another class.
This cheat sheet lists the things one can use when developing secure Node.js applications. Each item has a brief explanation and solution that is specific to Node.js environment. Node.js applications are increasing in number and they are no different from other frameworks and programming languages.
In this blog, I will show you how to use WebSockets support to build a fleet of serverless containers that make up a chatroom server that can scale a high number of concurrent connections (250,000 clients).

As part of YCW21, Dendron was eligible for significant credits from all major cloud providers. This articles goes over my experience redeeming credits in two in particular: AWS and Google Cloud.

Russian internet users began noticing something strange on Wednesday: a number of websites, including the Kremlin’s own Kremlin.ru, were down.
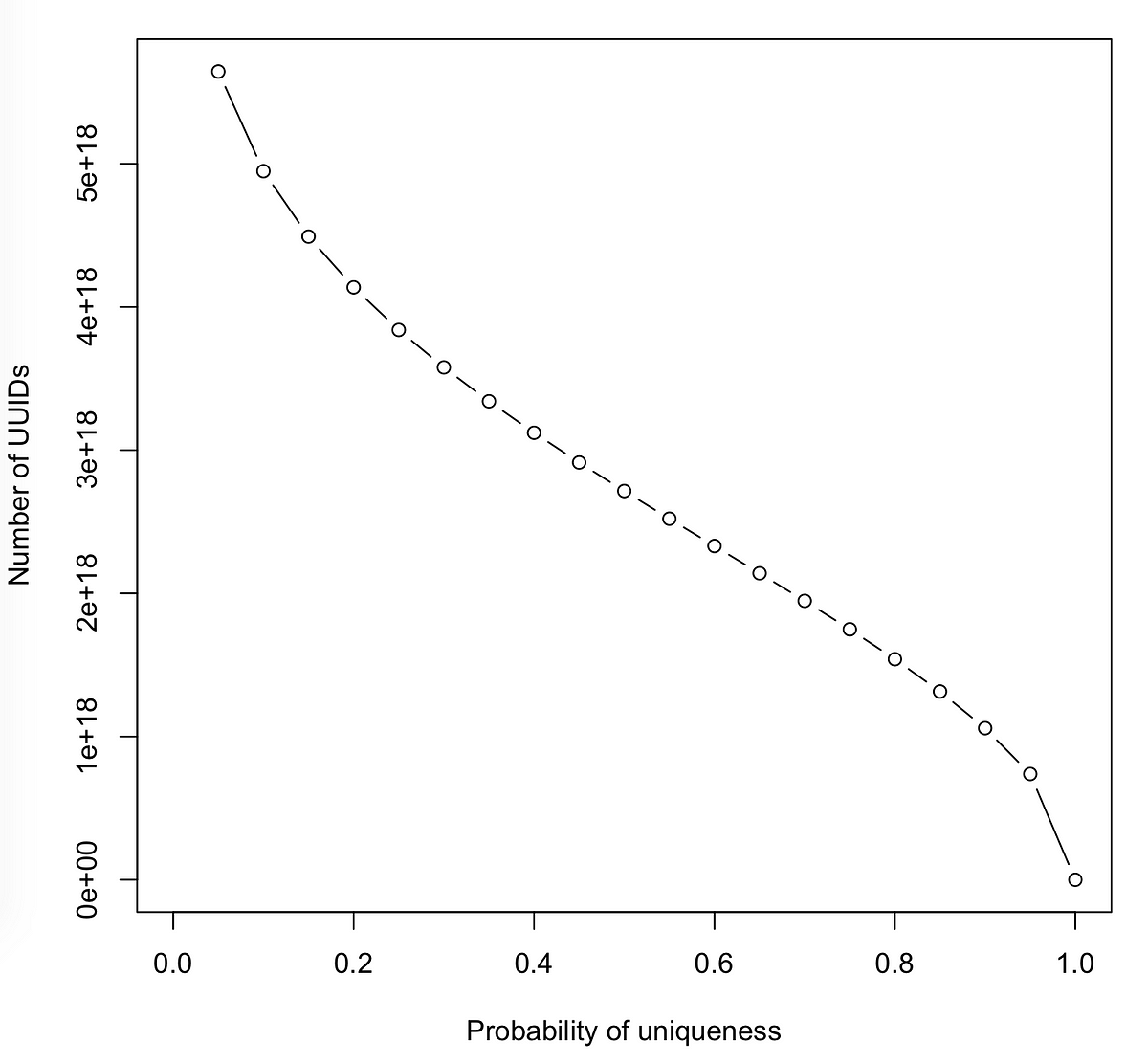
UUID stands for universally unique identifier. It looks like a 32-character sequence of letters and numbers separated by dashes. Some examples: UUIDs are handy for giving entities their own special names, for example, in a database.
Hi/Lo is a algorithm used for generating unique keys for use in a database as a primary key. It uses a sequence-based hi-lo pattern to generate values. It can be used with domain-driven design (DDD).
Thanks for your reading, save as your bookmark if you like my website.